
The Monero Project is currently investigating a potential compromise of the official website after a coin stealer was found in the Linux 64-bit command line (CLI) Monero binaries downloaded from the download page.
"CLI binaries available on http://getmonero.org may have been compromised at some point during the last 24h. Investigations ongoing," the Monero team said on Twitter.
As reported and confirmed by multiple users on GitHub, Reddit and Twitter, the Monero website delivered potentially malicious binaries with not matching hashes a little over 30 minutes. At the moment all binaries are clean as they are currently delivered from a secure fallback hosting server.
#Monero Security Warning:
— Monero || #xmr (@monero) November 19, 2019
CLI binaries available on https://t.co/UYopePqqdo may have been compromised at some point during the last 24h. Investigations ongoing.https://t.co/BqnONy4PPg
Users are encouraged by moderators on the Monero subreddit to "check the integrity of the binaries and verify that they were signed by Fluffypony's GPG key."
Guides on how to check if the downloaded binaries have the corrected hashes are available for Windows here and for Linux and macOS here.
Although Windows and macOS files haven't been reported to be compromised, users of all platforms should check the hashes for all downloaded Monero binaries since all of them could've been switched with malicious versions.
Correct hashes for all Monero binaries available for download on the official site are here: https://web.getmonero.org/downloads/hashes.txt.
If you downloaded binaries in the last 24h, and did not check the integrity of the files, do it immediately. If the hashes do not match, do NOT run what you downloaded. If you have already run them, transfer the funds out of all wallets that you opened with the (probably malicious) executables immediately, using a safe version of the Monero wallet (the one online as we speak is safe -- but check the hashes). More information will be posted as several people are currently investigating to get to the bottom of this. - Monero Core Team
Malicious binaries drop a coin stealer
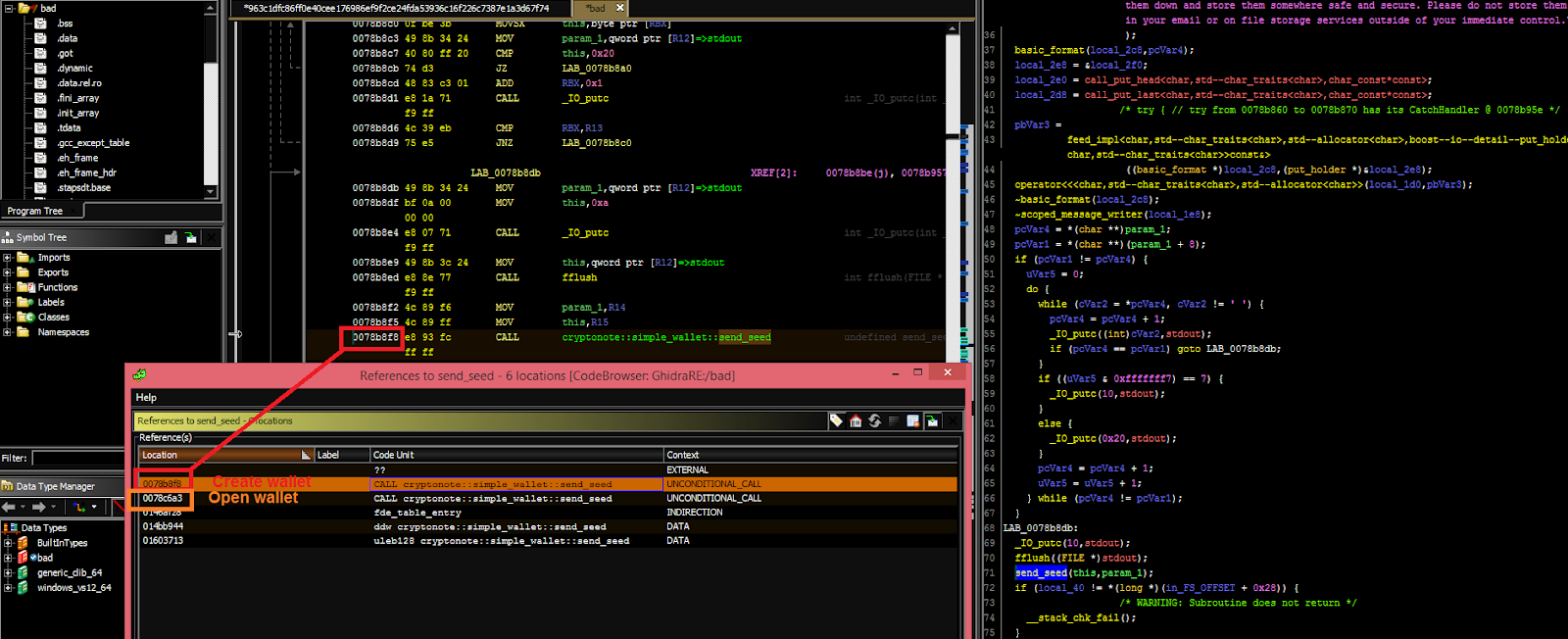
While a full analysis of the malicious Monero binaries that were distributed through the project's official download platform is not yet available, security researcher and contributor to the Monero project SerHack says that he was able to find a coin stealer embedded within.
"I can confirm that the malicious binary is stealing coins. Roughly 9 hours after I ran the binary a single transaction drained the wallet," moneromanz, one of the users who downloaded the compromised Monero binaries, confirmed. "I downloaded the build yesterday around 6pm Pacific time."
"I have not completed any malware analysis as of yet, but I'd like to get to the bottom of whether the binary is limited to stealing xmr, or also tries to compromise the machine as a whole or any of its files," he adds.
The malicious binaries downloaded from the official Monero website during the approximately 30 minutes window were also uploaded by moneromanz to an anonymous file hosting server and are available for analysis at https://anonfile[.]com/bbq8h9Bdn7/monero-wallet-cli.
H/T dark.fail
Update November 19, 17:31 EST: The Monero team published an update warning users that "the binaries of the CLI wallet were compromised for a short time," Monday 18th 2:30 AM UTC and 4:30 PM UTC:
Yesterday a GitHub issue about mismatching hashes coming from this website was opened. A quick investigation found that the binaries of the CLI wallet had been compromised and a malicious version was being served. The problem was immediately fixed, which means the compromised files were online for a very short amount of time. The binaries are now served from another, safe, source. See the reddit post by core team member binaryfate.
It's strongly recommended to anyone who downloaded the CLI wallet from this website between Monday 18th 2:30 AM UTC and 4:30 PM UTC, to check the hashes of their binaries. If they don't match the official ones, delete the files and download them again. Do not run the compromised binaries for any reason.
We have two guides available to help users check the authenticity of their binaries: Verify binaries on Windows (beginner) and Verify binaries on Linux, Mac, or Windows command line (advanced). Signed hashes can be found here: https://getmonero.org/downloads/hashes.txt.
The situation is being investigated and updates will be provided soon.
Update November 19, 18:16 EST: Bart Parys took a closer look at the compromised binaries and discovered that the Linux sample was infected with a coin stealer malware.
He was also able to get a Windows malware sample from the attackers' command and control (C2) server that, just like its Linux counterpart, steals the seed and attempts to exfiltrate funds from the victims' wallets.
Blaze also provides a detailed procedure for detecting the malware including network traffic logging and a Yara rule, recommendations on how to restore your seed or account, and indicators of compromise (IOCs) at the end of his analysis.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now